IEEE 802.1X
From Zenitel Wiki
IEEE 802.1X is an IEEE Standard for port-based Network Access Control (PNAC). By "port" we mean a single point of attachment to the LAN infrastructure. It provides an authentication mechanism to devices wishing to attach to a LAN, either establishing a point-to-point connection or preventing it if authentication fails.
Contents
User interface
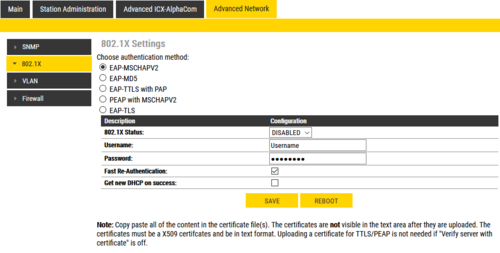
The 802.1X configuration is done from the IP-station web interface at Advanced Network > 802.1X.
Choose authentication method. The different authentication methods are:
- MSCHAPV2
- MD5
- TTLS with PAP
- PEAP with MSCHAPV2
- TLS
MSCHAPV2 and MD5 encrypts the password.
TTLS with PAP and PEAP with MSCHAPV2 encrypts both username and password.
Depending on the authentication method there are a few parameters to configure.
- 802.1X status: Enable or disable 802.1X
- Username: The username used to identify a station.
- Password: The password associated with the username.
- Fake username ["TTLS with PEAP" and "PEAP with MSCHAPV2" only]: The fake username sent outside of encrypted tunnel with TTLS with PAP and PEAP with MSCHAPV2. The user name is encrypted.
- Verify server with certificate [TTLS with PEAP, PEAP with MSCHAPV2 and TLS only]: Specifies that the client verifies that server certificates presented to the client have the correct signatures, have not expired, and were issued by a trusted root certification authority (CA). It's enabled by default.
- Fast Re-Authentication: EAP peer and an EAP server authenticate each other through a third party known as the EAP authenticator. When a peer moves from one authenticator to another, it is desirable to avoid a full EAP authentication to support fast handovers.
- Get new DHCP on success: If 802.1X authentication is successful, station will restart it's DHCP client.
- Insert CA Certificate [TTLS with PEAP, PEAP with MSCHAPV2 and TLS only]: Upload certificate (public key) used by authentication server. This is not required if "Verify server with certificate" option is disabled.
- Insert User Public Certificate [TLS only]: Upload certificate (public key) used by authentication client (user).
- Insert User Private Key [TLS only]: Upload the private key which is paired with user public certificate.
- Click Save to save the current settings
- Click Reboot. The new 802.1X settings will only come into effect after a reboot.
Software requirement
802.1X is supported:
- In INCA stations as from firmware 1.09.3.0.
- In Turbine stations in all firmware versions.
- In Pulse mode as from firmware 4.7 (Turbine) and 2.7 (INCA). (Previously supported only in SIP and AlphaCom mode).
- In ICX-AlphaCom, as from software version 1.1.3.0
802.1X and software upgrade
Turbine devices with Dual Partitions
On Turbine Devices with Dual Partitions, software upgrade can be performed also when the station is using 802.1X authentication.
This is applicable to all devices that come with firmware 5.1 or higher preinstalled from factory.
INCA stations and Turbine devices with single partition
On the following devices a software upgrade is not possible when the station is using 802.1X authentication:
- INCA stations
- Turbine devices with firmware 5.0 or earlier preinstalled from factory (Note that it is not sufficient to upgrade the firmware to version 5.1 or higher "in the field").
In order to upgrade these stations, one must either:
- Remove security on the switchport, upgrade and set security back on the switchport.
- Connect the station to a non-802.1X port and do a manual upgrade.
Note that in the Turbine stations the 802.1x certificate does not survive a software upgrade. The certificate must be uploaded to the station again after a software upgrade.
The reason that the station cannot be upgraded is that during the upgrade of the IP-station, 802.1X will not be running. Thus if 802.1X reauthentication is enabled and is performed during upgrade, the IP-station will lose contact with the tftp server (dependent on the configuration when 802.1X authentication fails). If the IP-station loses contact with the tftp server, it will not be upgraded. The same is also valid when upgrading via VS-IMT.